In today’s digital age, receiving an email claiming that your account has been compromised can send anyone into a panic. These alarming messages – often accompanied by screenshots of your inbox or threats to expose personal information unless you pay a ransom – are designed to provoke fear and urgency. But before you react impulsively, it’s crucial to stay calm and assess the situation. Whether it’s a legitimate breach or a clever phishing scam, this comprehensive guide on email hacked: What to Do If You Get an Email Saying You’ve Been Hacked will walk you through the essential steps to protect your data, finances, and peace of mind.
Understanding the Email: Is It a Real Hack or a Scam?
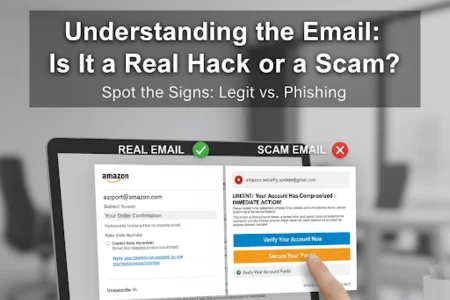
Common Types of “Hacked” Emails
Scammers often use tactics like spoofing to make emails appear legitimate. For instance, you might receive a message from what looks like your own email address, stating, “I’ve hacked your account and have access to your webcam.” This is a classic sextortion scam, where the sender claims to have compromising videos or data. In reality, they might have obtained your email from a public data leak and are bluffing.
On the other hand, legitimate notifications come from trusted sources like Google, Microsoft, or your bank. These usually include specific details about suspicious activity, such as logins from unfamiliar locations, and prompt you to secure your account without demanding payment.
How to Verify the Claim
To check if your account is truly hacked, avoid clicking any links in the suspicious email. Instead, log in directly to the affected service via its official website or app. For email providers like Gmail or Outlook:
- Review your recent activity log. Gmail’s “Last account activity” section shows IP addresses and devices used to access your account.
- Check for forwarded emails or unfamiliar filters that could be diverting messages.
- Use tools like Have I Been Pwned? (Use a free online tool to check if your email has been exposed in reported data breaches.
If the email mentions a password, test it on a non-critical site or change it immediately if it’s current. Remember, if the sender provides an old password, it could be from a past breach, not a current hack.
Differentiating between scams and real threats is key. Scams often include urgency, poor grammar, or requests for cryptocurrency payments. Real hacks might involve actual data exposure, like leaked photos or financial details. If unsure, consult a cybersecurity expert or use antivirus software to scan your devices.
Immediate Actions: Secure Your Accounts Right Away

Once you’ve received such an email, time is of the essence. Delaying could allow hackers to cause more damage. Here’s what to do if you suspect your email has been hacked.
Change Your Passwords Immediately
Start with the affected email account. Generate a secure, distinct password with at least 12 characters, mixing uppercase and lowercase letters, numbers, and special symbols. Avoid reusing passwords across sites—use a password manager like LastPass or Bitwarden to generate and store them securely.
If the hack extends to linked accounts (e.g., social media or banking), update those too. Prioritize high-risk ones first: financial apps, e-commerce sites, and work emails.
Enable Two-Factor Authentication (2FA)
Two-factor authentication enhances account protection by requiring an additional verification step, such as a code sent to your mobile device. Enable it on all accounts that support it. For email, options include app-based authenticators (e.g., Google Authenticator) or hardware keys like YubiKey, which are more secure than SMS.
If your phone number is compromised, switch to authenticator apps to avoid SIM-swapping attacks, where hackers hijack your number.
Disconnect Unauthorized Devices
From your account settings, review and revoke access from unknown devices. For example, in Gmail, go to “Manage your Google Account” > “Security” > “Your devices” and sign out from suspicious ones. Do the same for other platforms like Facebook or Amazon.
Assess the Damage: What Has Been Compromised?

After securing your accounts, evaluate the extent of the breach. This step is vital for minimizing fallout.
Check for Data Exposure
Scan your email for sent messages you didn’t authorize – these could include spam to your contacts or fraudulent transactions. Review bank statements for unauthorized charges and monitor credit reports via services like Equifax or TransUnion.
If personal data like Social Security numbers or addresses were in your email, consider freezing your credit to prevent identity theft.
Run Antivirus Scans
Use reputable antivirus software (e.g., Malwarebytes or Norton) to scan all devices connected to your email. Look for malware like keyloggers that could have captured your credentials. Consistently update your operating system and apps to patch vulnerabilities and protect against cyber risks.
Notify Affected Parties
If a work email is compromised, promptly notify your IT team for swift action.. For personal contacts, send a warning email (from a secure account) explaining the situation and advising them not to open suspicious links from you.
In cases of financial compromise, contact your bank or credit card issuer to dispute charges and request new cards.
Reporting the Incident: When and How to Involve Authorities

Not every hacked email requires police involvement, but serious cases do.
Report to Cybersecurity Agencies
In the US, file a report with the FBI’s Internet Crime Complaint Center (IC3). In the EU, inform your national data protection agency, including specifics like the email’s content, sender details, and any demands made.
Legal Considerations
If the hack involves ransomware or extortion, avoid paying – it funds criminals and doesn’t guarantee data safety. Instead, preserve evidence: screenshot the email, note headers (right-click and view source), and save attachments without opening them.
Consult a lawyer if sensitive business data is involved, as you may need to comply with data breach notification laws like GDPR or CCPA.
Long-Term Recovery: Rebuilding Your Digital Security
Recovering from a potential hack isn’t just about immediate fixes; it’s about strengthening your defenses.
Update All Software and Devices
Outdated software is a hacker’s playground. Enable automatic updates on your phone, computer, and router. Consider upgrading to a more secure router with built-in firewall features.
Educate Yourself on Phishing Prevention
Phishing is often how hacks start. Learn to spot red flags: unsolicited attachments, mismatched URLs (hover over links), or requests for personal info. Employ browser add-ons like uBlock Origin to filter out dangerous websites and phishing attempts.
Use Secure Email Practices
Switch to encrypted email services like ProtonMail for sensitive communications. Avoid public Wi-Fi for logging into accounts, or use a VPN like ExpressVPN to encrypt your connection.
Monitor Your Online Presence
Set up alerts for your email on breach notification sites. Regularly Google yourself to check for exposed data and request removals from data broker sites like Spokeo.
Prevention Strategies: How to Avoid Future Hacks

Prevention is better than cure. Implementing these habits can drastically reduce your risk.
Strong Password Hygiene
Ditch simple passwords like “123456” or “password.” Use passphrases, e.g., “BlueSky2025!RainyDay.” Rotate them every 3-6 months, especially after breaches.
Multi-Layered Security
Beyond 2FA, enable biometric logins where possible. Use email aliases for sign-ups to compartmentalize risks.
Backup Your Data
Regularly back up emails and files to an external drive or cloud service like Google Drive (with encryption). This ensures you can recover without paying ransoms.
Stay Informed on Cyber Threats
Follow cybersecurity blogs like Krebs on Security or subscribe to newsletters from sources like CISA (Cybersecurity and Infrastructure Security Agency). Attend webinars or use apps like Duo Mobile for security tips.
For Businesses: Additional Measures
If this involves a corporate email, implement employee training programs on cybersecurity. Utilize business-grade solutions like Microsoft Defender to identify and mitigate sophisticated cyber threats.
Case Studies: Real-World Examples and Lessons Learned
To illustrate, consider the 2023 MOVEit data breach, where hackers exploited software vulnerabilities, affecting millions. Victims who acted quickly by changing passwords minimized damage.
Another example is the 2018 Yahoo breach, exposing 3 billion accounts. Individuals who disregard hack alerts risk persistent spam and potential identity fraud.. Lessons: Always verify and act promptly.
In a personal story, a freelance writer received a “hacked” email with an old password. By checking Have I Been Pwned?, she discovered it from a 2012 LinkedIn leak—not a current hack. She updated everything and avoided the scam.




